Static Source Code Analysis Tools
Detection of vulnerabilities and run-time errors
CodeSonar


CodeSonar allows to check the adherence of the source code to "Safety" and "Security" software coding standards, as required by the main Functional Safety standards.
Programming languages




Safety standards
C 2012
C++ 2008
C++ 14, 2018
Security standards

C 2016
C++ 2016



CodeSonar includes various programs that detect potential run-time errors.
CodeSonar allows you to verify that the developed source code complies with the selected security standards. For each standard, you can select the rules you want to verify.
The end result guarantees the safe use of the programming language and the portability of the application.
Run-time error detection
- Null pointer usage
- Buffer overflows
- Unreleased dynamic memory
- Type conversion problems
- Variable initialization errors
- Improper use of library functions
- Detection of invalid loops and cycles
- Dead code detection
- Concurrency errors
- And many others
CodeSonar's differentiating features
Depth of Analysis
One of the differentiating factors of CodeSonar is it's ability to perform deep code analysis, including control flow and data flow analysis, allowing to obtain errors that affect different functions in different files.
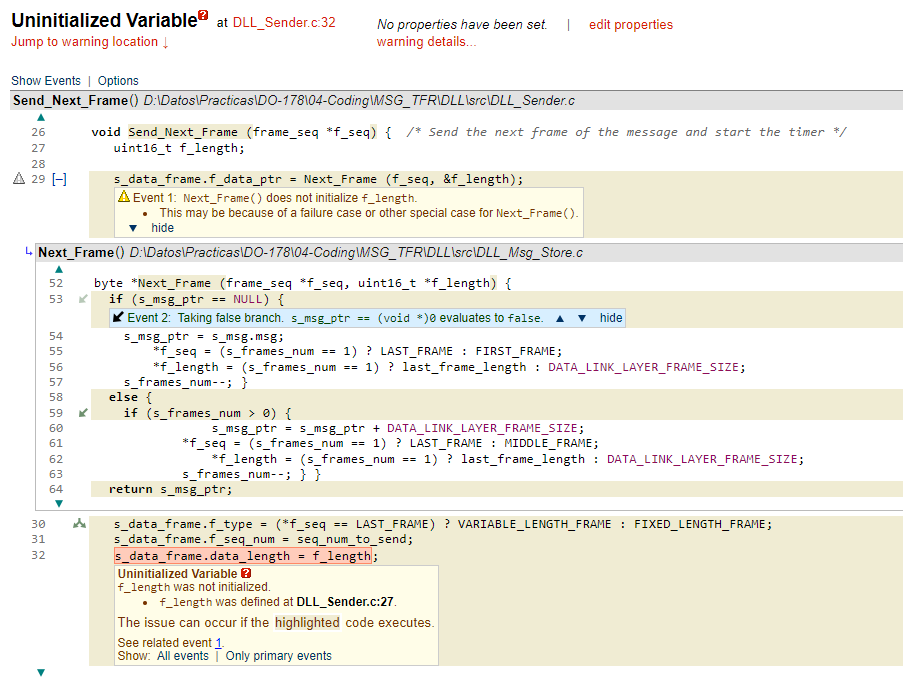
CodeSonar distinguishes between errors and warnings of different severity. Once an error is identified, the sequence of function calls that cause it and the statement and condition where the error occurs are displayed. This is marked as a sequence of events.
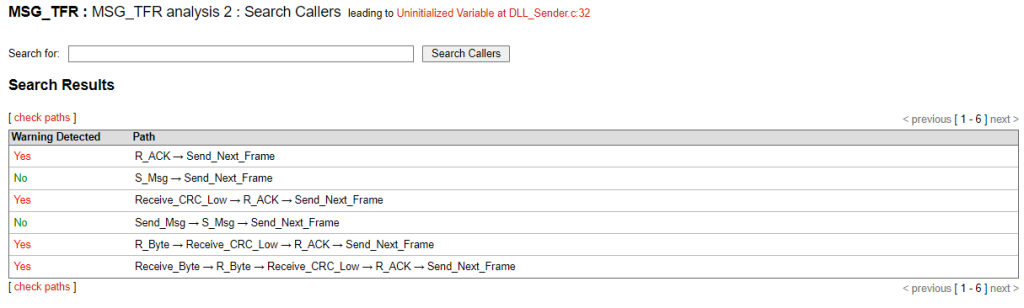
CodeSonar finds errors that other static code analysis tools are unable to locate.
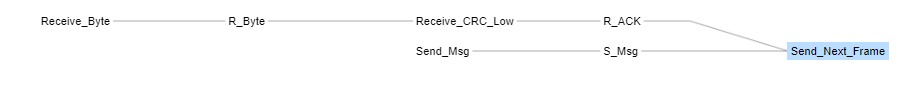
The paths and the tree of calls leading to the error can also be displayed.
In this example of a local variable initialization error to a function, CodeSonar detects that the error occurs in four execution paths out of the six possible ones.
Scalability: Distributed Analysis
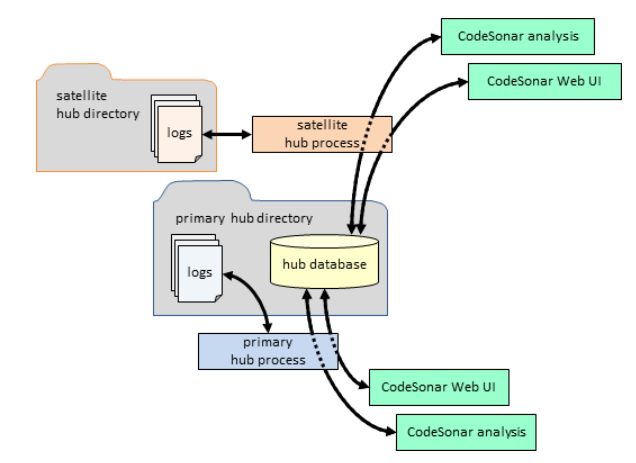
CodeSonar enables the analysis of very large source code repositories at a very high level of analysis depth by being able to distribute the analysis among multiple processes running on different servers.
CodeSonar manages a primary Hub process for analysis and web visualization and, optionally, several satellite Hub processes. The primary and secondary processes share the same database.

DevSecOpcs Integration
CodeSonar integrates with various continuous integration environments: Jenkins, GitLab, GitHub, etc.
The developer can visualize and correct security issues within the CI/CD environment and access more detailed information in the Hub with a simple mouse click. If errors are detected, defects can be opened in specialized tools such as Jira. The project manager or quality managers can check the security status using the reports included within the CI/CD environment. The analysis load can be distributed among multiple processes running on different servers.
CodeSonar manages a primary Hub process for analysis and web visualization and, optionally, several satellite Hub processes. The primary and secondary processes share the same database.
Integration with other tools

CodeSonar allows the use of different cross-compilers for PowerPC and ARM architectures. In addition, it provides a graphical wizard to define the different analysis parameters and capture all the necessary information for building the executable using each manufacturer's build method.
Once the compiler and linker information, compilation options, include directories, and pre-processor macros have been captured, CodeSonar is able to analyze the source code using all that information.
Compilers supported by CodeSonar
ARM Real View & Clang
Borland
Clang
CodeVision
Cosmic
CodeWarrior
Green Hills C/C++
GNU C/C++
Keil
Hi-Tech
IAR
Intel
Microsoft
MPLAB
QNX
Renesas
SHARC, Blackfin
Tasking
Texas Instruments
Wind River
CodeSonar for Java and C#
Security vulnerability detection
Injections
Cookies
Passwords
LDAP
Cryptographic errors
Reference to external entities
And many others
Supported C# Platforms
MVC
Unity
Web Forms
Windows Forms
Supported Java Platforms
Apache-CXF
AspectJ
EJB
JAX-RS
JAX-WS
JPA
JSF
Jersey
RESTeasy
RESTlet
Servlet
Spring
Android