Static Binary Code Analysis Tools
Vulnerability detection
CodeSentry

CodeSentry is a static analysis tool for binary software composition.
CodeSentry allows detecting vulnerabilities in third-party software present in applications or products.
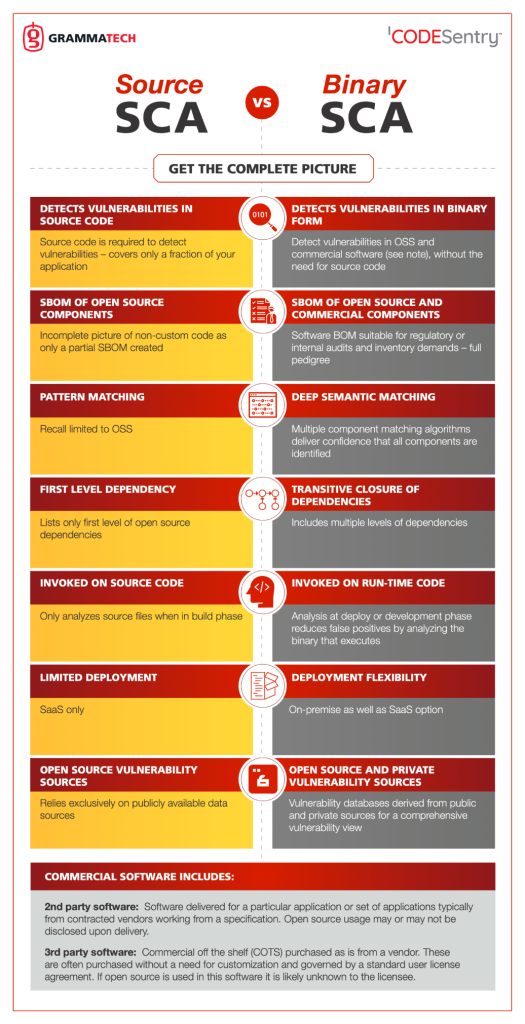
Binary Software Composition Analysis (SCA)
Binary Software Composition Analysis allows detecting vulnerabilities in third-party software present in applications or products.
90% of companies use third-party software in their applications. In addition, a large part of commercially purchased applications incorporate third-party software . Finally, applications developed by third parties for a company may incorporate third-party software .
A significant portion of applications contain components with a high level of known vulnerabilities. Some of the latest vulnerabilities that have caused problems in the industry are:
Hearbleed bug (CVE-2014-0160): Vulnerability in the OpenSSL cryptographic library
Urgent/11: Vulnerability in the TCP/IP stack originally developed by Interpeak. Exploiting the vulnerability allowed code to be executed remotely. It has impacted real-time operating systems such as ENEA, Green Hills Integrity, Mentor and Wind River VxWorks.
Ripple20: Vulnerability in the TCP/IP stack. Exploiting the vulnerability allowed code to be executed remotely. It has affected products from HP, Schneider Electric, Intel, Rockwell Automation, Caterpillar, Baxter and many others.
CodeSentry analyzes the final executable in binary format instead of the source code, which in many cases is not available. This technique is very reliable and significantly reduces the number of false positives as it eliminates the analysis of disabled code or code that is ultimately not present in the executable object code.
CodeSentry Functionality
CodeSentry incorporates deep binary software analysis utilities, generates a Software Bill of Materials inventory and accesses the most complete databases of known vulnerabilities on the market.
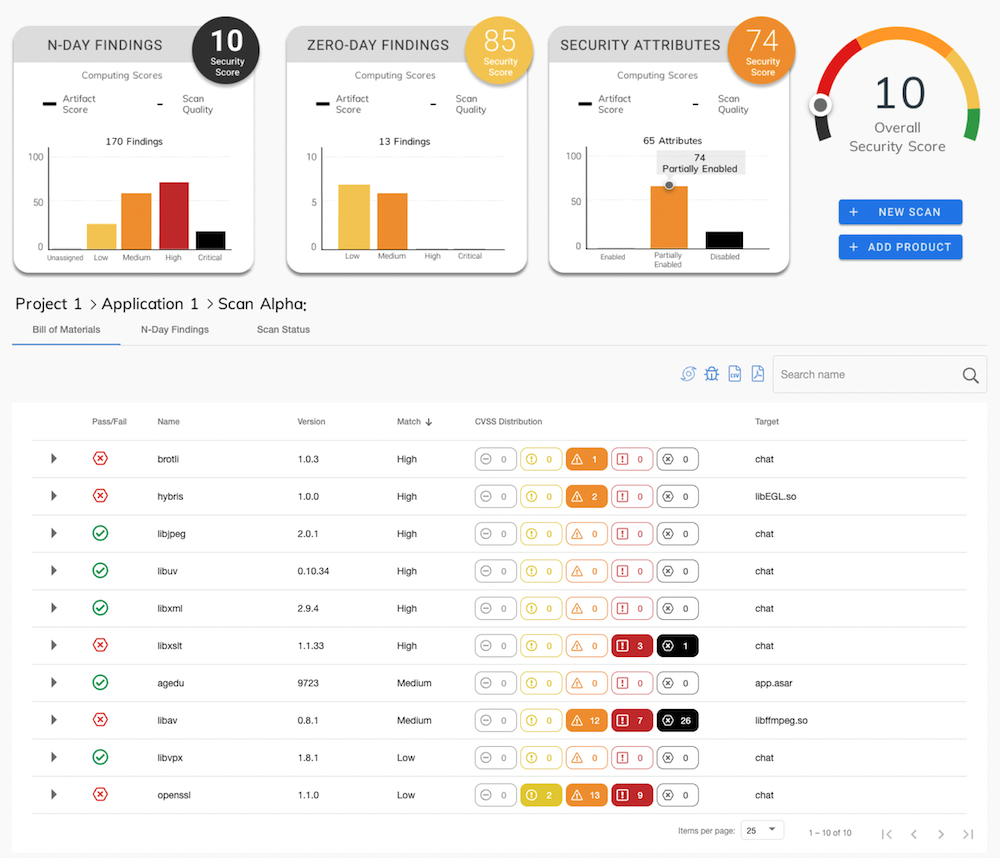
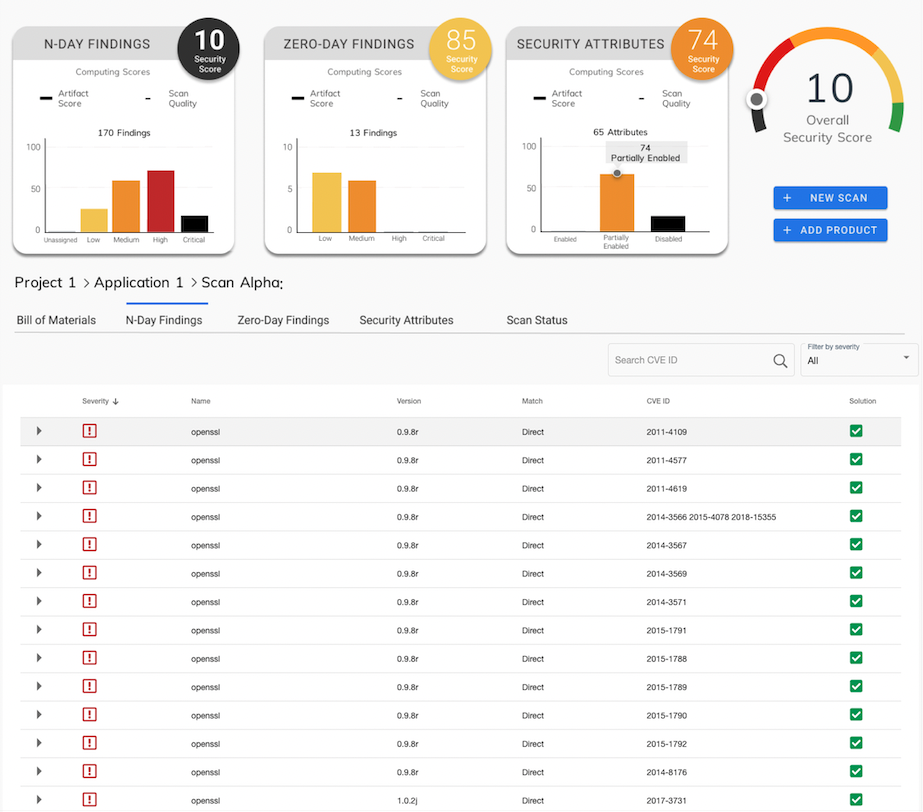
The figure shows the list of components that make up the application inventory.
For each component, the version, the degree of similarity with the analyzed library and the number of vulnerabilities detected according to the CVSS (Common Vulnerability Scoring System) risk measurement, which classifies them into low, medium, high and critical severity degrees, are shown.
Additionally, CodeSentry generates, for each component present in the inventory, reports of N-Day (known) vulnerabilities, based on public vulnerability databases, and Zero-Day (potential vulnerabilities), based on the tool's binary code analysis capabilities.
Supported formats of the application to be analyzed
- Compressed Formats
- Zip (.zip)
- 7-zip (.7z)
- Bzip (.bz2)
- Gzip (.gz)
- Windows installers (.msi)
- Native binary formats
- Linux (.o, .so, .a)
- Windows (.exe, .obj, .dll)
- MacOS
- Crossed binary formats
- Intel
- ARM
Roadmap: Upcoming formats to be supported
- Disk images
- Installer images
- Containers
- Directories
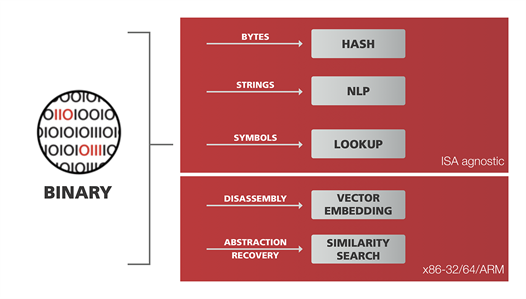
In-depth analysis of binary code
CodeSentry uses multiple pattern matching algorithms for both native compilers and cross-compilers for Intel and ARM architectures.